Gpg Tools For Mac
Step 1: Install software
We use the Homebrew package manager for this step.

Step 2: Update ~/.gnupg/gpg-agent.conf
If this file does not exist, create it.
Step 3: Update or Create ~/.gnupg/gpg.conf
If this file does not exist, create it.
Step 4: Modify your Shell
- The bundle id for Gpg Tools for Mac is com.tomsci.GpgTools. The application lies within Security Tools, more precisely General. This free software for Mac OS X is a product of gpgtools. The most popular versions of Gpg Tools for Mac are 2014.11, 2011.07.11 and 2011.07.
- Install GPG Suite on Mac OSX. June 23, 2017 Amber. App name: GPG Suite. Install Spring Tool Suite on Mac OSX; Install freeling on Mac OSX.
GnuPG, also known as GPG, is a command line tool with features for easy integration with other applications. A wealth of frontend applications and libraries are available. GnuPG also provides support for S/MIME and Secure Shell (ssh). Since its introduction in 1997, GnuPG is Free Software (meaning that it respects your freedom).
Append the following to your ~/.bash_profile or ~/.bashrc or ~/.zshrc
Step 5: Restart your Terminal or source your ~/.*rc file
Step 6: Update the Permissions on your ~/.gnupg Directory
You will need to modify the permissions to 700 to secure this directory.
Step 7: Create your GPG Key
Run the following command to generate your key, note we have to use the --expert flag so as to generate a 4096-bit key.
Step 8: Answer the Questions
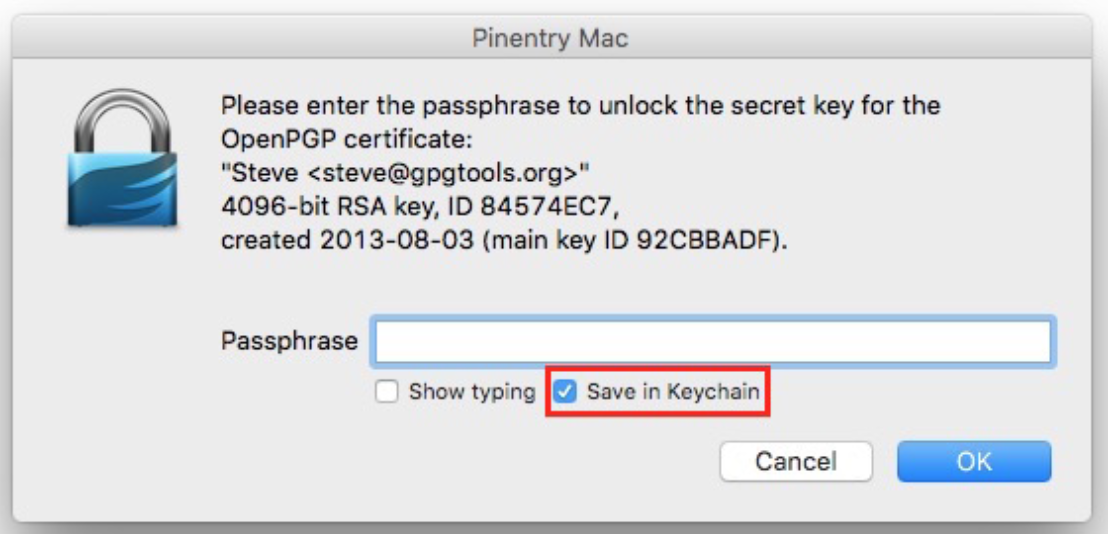
Once you have entered your options, pinentry will prompt you for a password for the new PGP key.
Step 9: Get your key info for Git, etc.
Step 10: Get your key id
Use the next command to generate a short form of the key fingerprint.
Copy the text after the rsa4096/ and before the date generated and use the copied id in step 13:
You need to copy the output similar to the example above where the ######## is.
Step 11: Export the fingerprint
Gpg Keychain For Windows 10
In the output from step 10, the line below the row that says 'pub' shows a fingerprint-this is what you use in the placeholder. The output from below is what you copy to Github:
Step 12: Configure Git to use gpg
Gpg Tools For Mac
Step 13: Configure Git to use your signing key
The below command needs the fingerprint from step 10 above:
Step 14: Configure Git to sign all commits (Optional-you can configure this per repository too)
This tells Git to sign all commits using the key you specified in step 13.
Step 15: Perform a Commit
Step 16: Pinentry Prompt
You will now be prompted by Pinentry for the password for your signing key. You can enter it into the Dialog box-with the option of saving the password to the macOS X Keychain.
Step 17: Submit your PGP key to Github to verify your Commits
Login into Github.com and go to your settings, SSH and GPG Keys, and add your GPG key from the page.
Step 18: Submitting Your Key to a Public Keyserver (very optional)

Before you jump on submitting your key to a service such as the MIT PGP Key Server, you should consider the following:
- You cannot delete your key once submitted
- Spammers have been known to harvest email addresses from these servers
- If you're only signing your Git commits to Github this isn't necessary
If you have any errors when generating a key regarding gpg-agent, try the following command to see what error it generates:
I don’t like GPGTools. I want GPG on macOS. Every tutorial has some obsolete part. Here’s what I did.
GPGTools installs a lot of things that I don’t want to use. I just want to sign my commits on GitHub and save my GPG key in macOS keychain.
There are two main dependencies to achieve that, gnupg contains the GPG tools to generate keys and sign things, as well as an agent to do agent things; and pinentry-mac which is the part of GPGTools that prompts for your key password and stores it on the OS keychain.
Gpg For Windows
GPG Setup
Before anything, install homebrew.
After that, install the dependencies:
Then, let’s generate your first key. I recommend using RSA and RSA, a key size of 4096, and not having the key expire. Remember to choose a strong password.
Now you need to configure gpg-agent to use pinentry-mac by creating a file ~/.gnupg/gpg-agent.conf:
Then, sign a test message so pinentry-mac can store your password in the keychain:
Gpg Tools For Mac Os X
This should open a dialog prompting your password. Remember to check “Save in Keychain”.
Connecting to GitHub
First, copy your private key to add to GitHub:
And paste it in GitHub’s Settings > SSH and GPG keys > New GPG key.
Second, configure your git environment to use signed commits. I’ve done it globally. First obtain your public GPG keys:
Then configure git:
And finally, commit something with the-S argument to make sure it’s signed:
Troubleshooting

Things you can try if things are not working:
Cover photo by Micah Williams on Unsplash.
